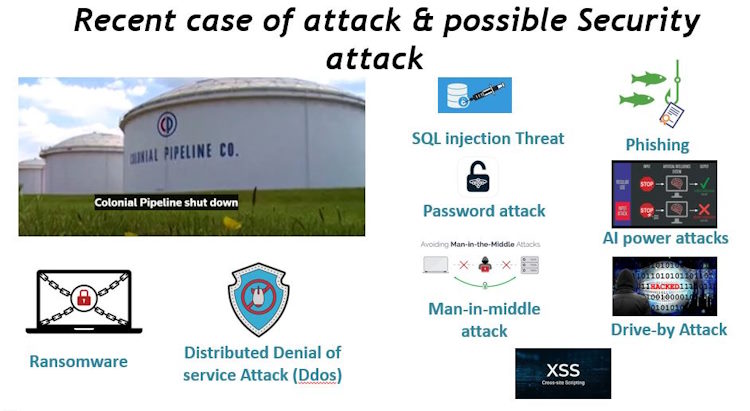
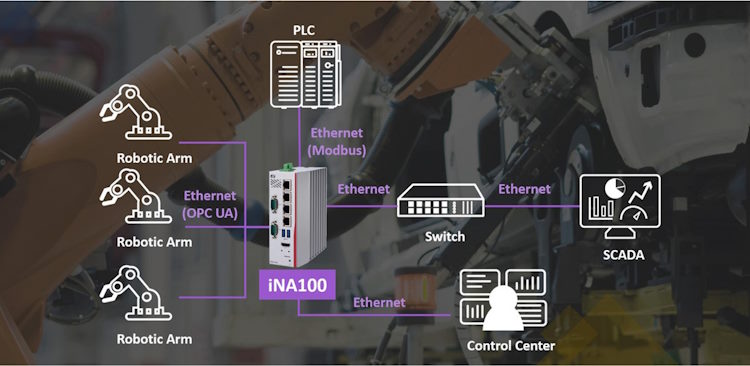
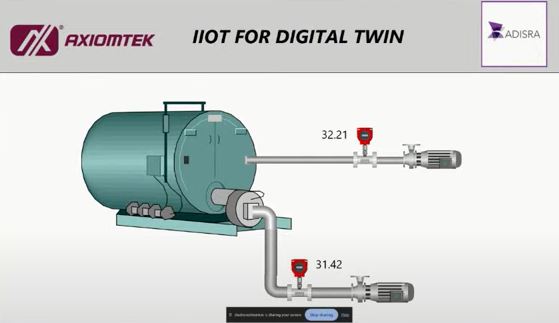
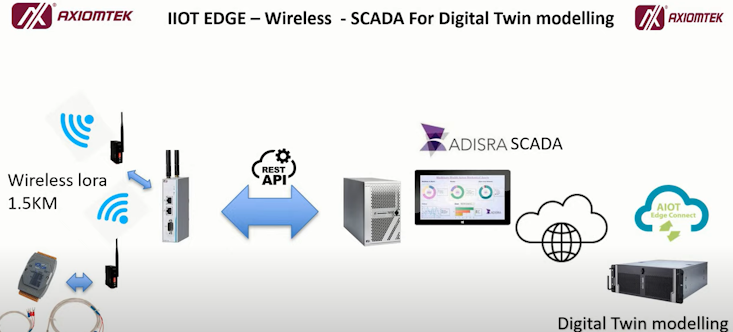
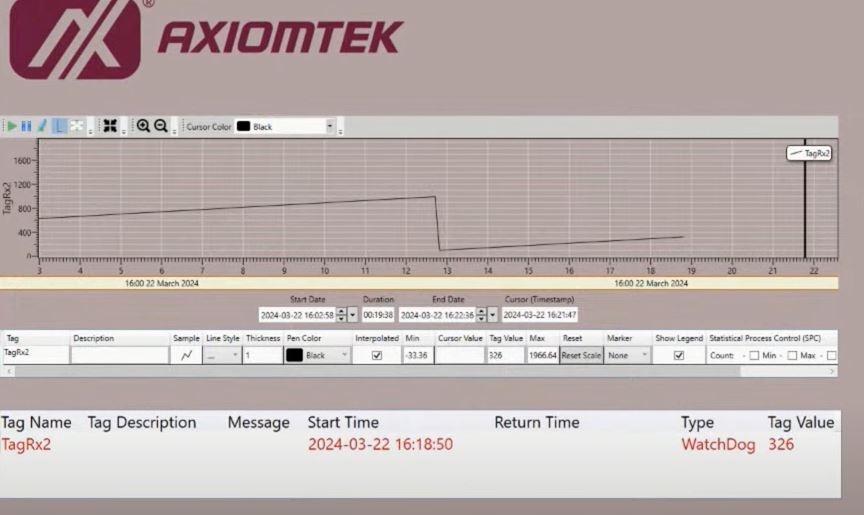
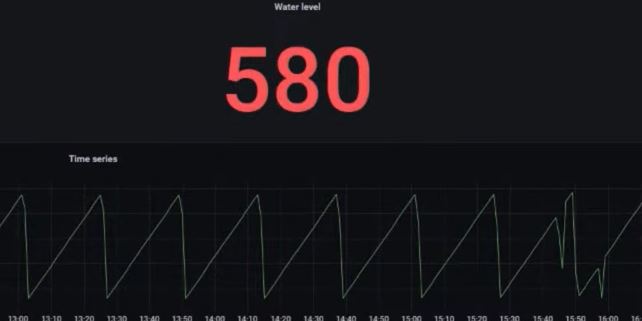
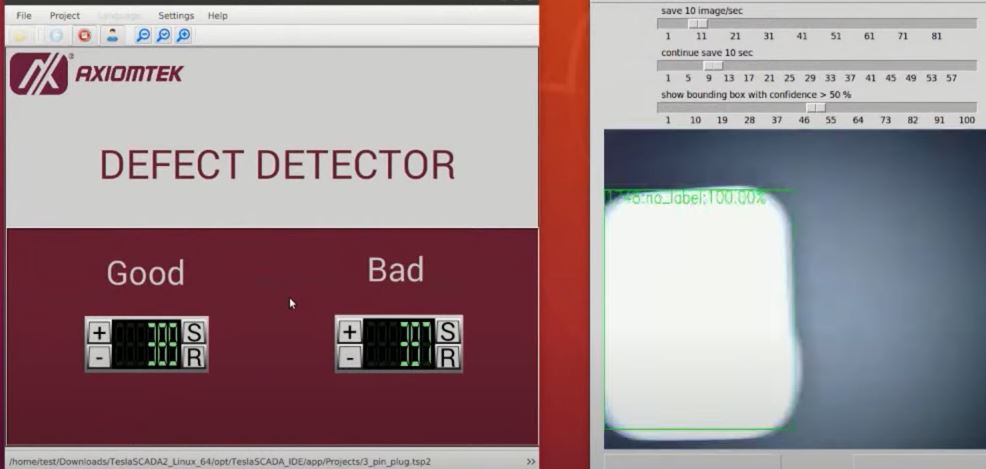
The primary focus of the discussion was on smart supply chain management utilizing AI and IoT. This topic was presented by Mr. CC Lee, our technology trainer and technology public speaker, along with Mr. Tan Kien Leong, the AIoT trainer and solution architect from AIoTmission Sdn Bhd.
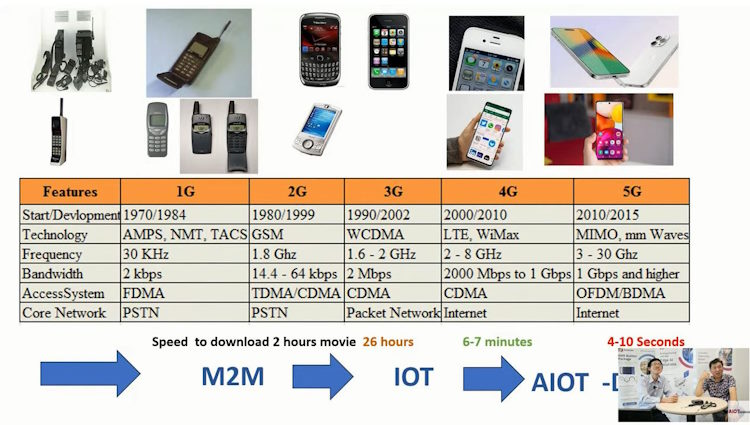
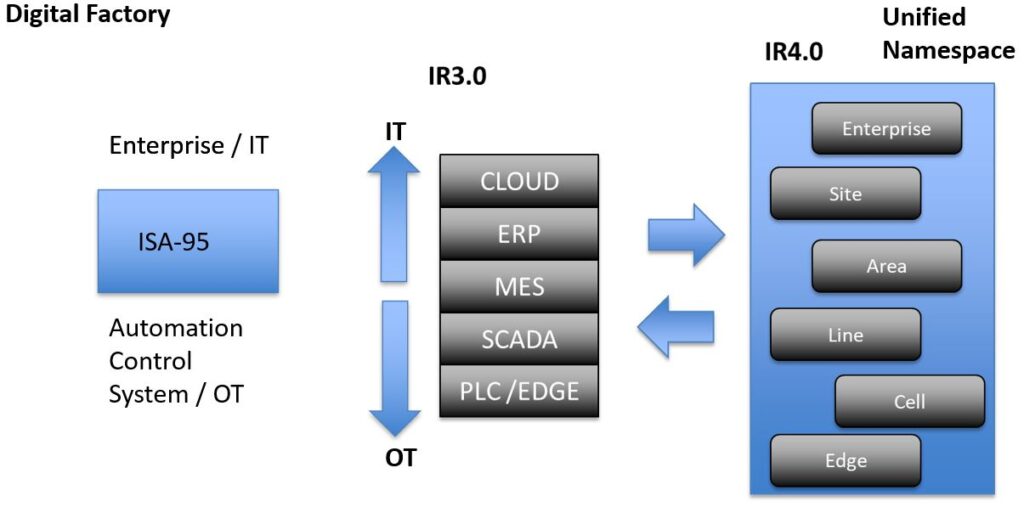
The Fourth Industrial Revolution (IR4) brings numerous advanced technologies that can significantly enhance smart supply chain management. Key technologies include:
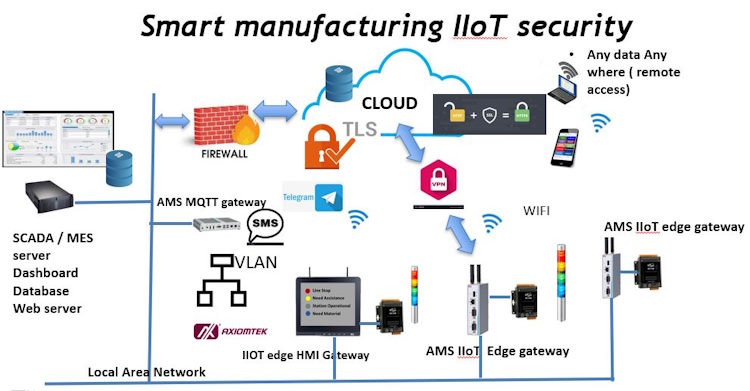
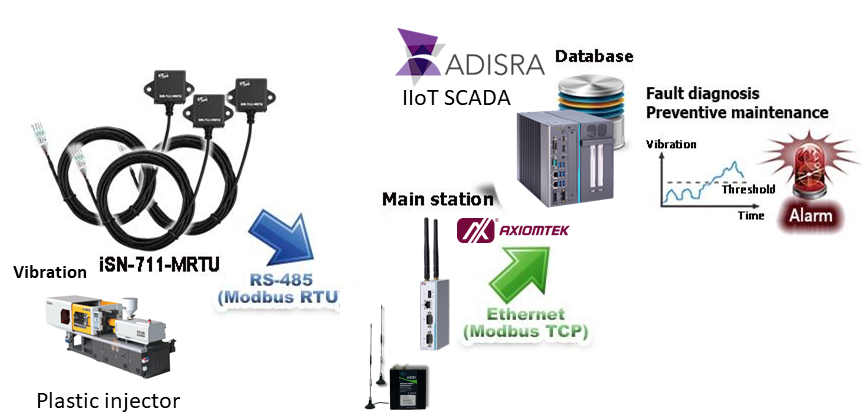
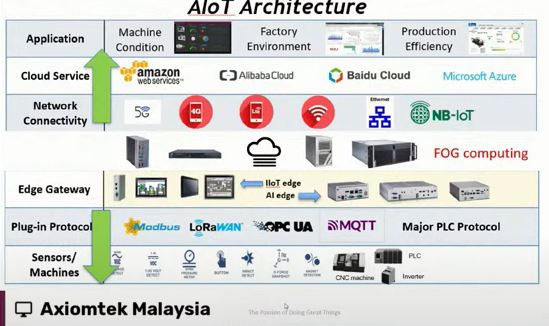
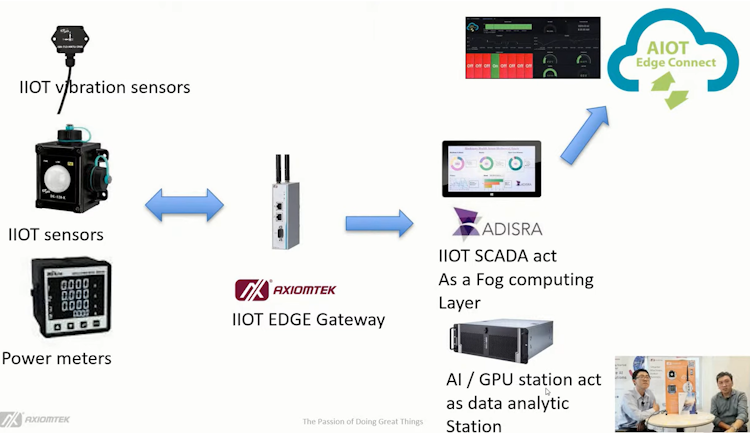
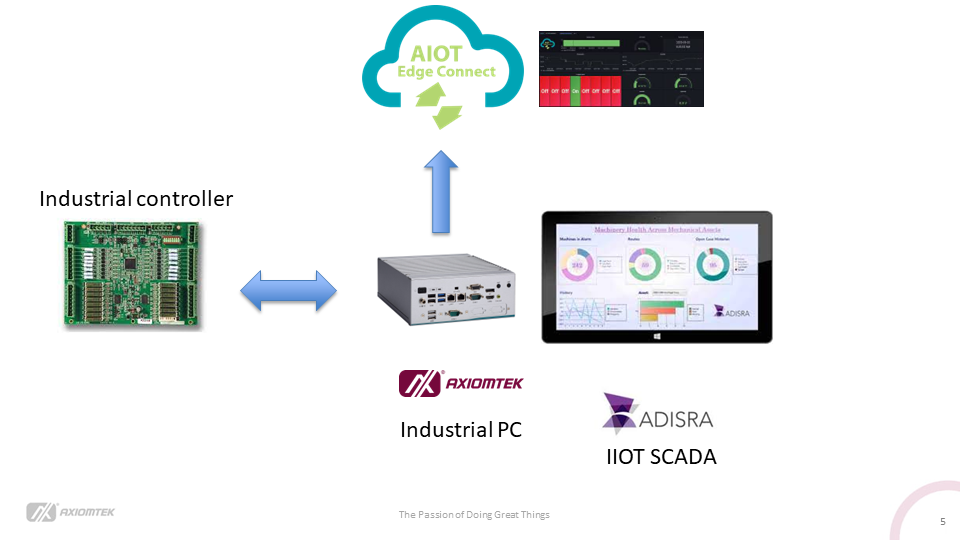
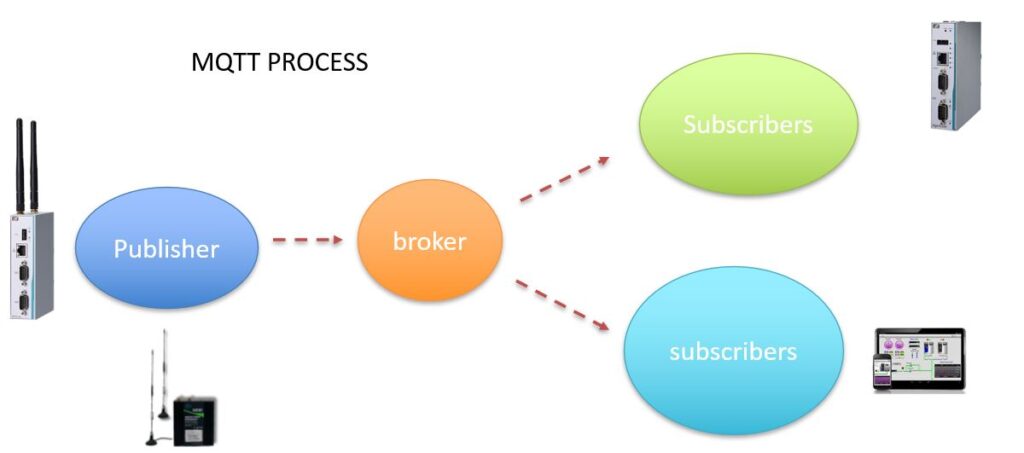
Internet of Things (IoT): Smart Sensors: Enable real-time tracking of goods and assets, monitoring conditions like temperature and humidity. RFID Tags: Facilitate automated inventory management and asset tracking.
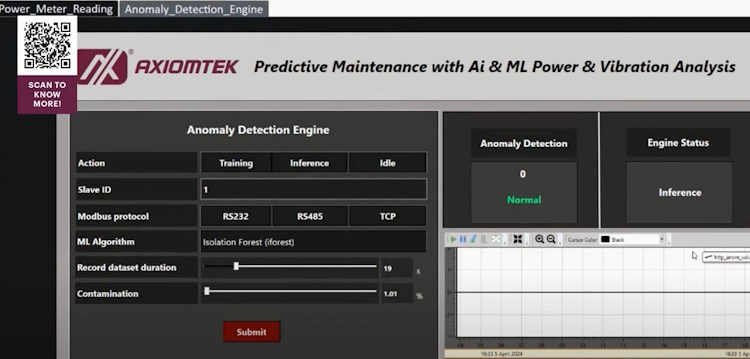
Artificial Intelligence (AI) and Machine Learning (ML): Predictive Analytics: Improve demand forecasting and inventory management. Automated Decision-Making: Enhance supply chain efficiency by optimizing routes, scheduling, and resource allocation.
Blockchain: Transparency and Traceability: Provide an immutable record of transactions, ensuring authenticity and reducing fraud. Smart Contracts: Automate and enforce contractual agreements without intermediaries.
Big Data Analytics: Data Integration: Combine data from various sources for comprehensive insights. Trend Analysis: Identify patterns and trends to improve supply chain strategies.
Cloud Computing: Scalability: Easily scale up or down computing resources based on demand. Collaboration: Facilitate seamless collaboration and information sharing across the supply chain.
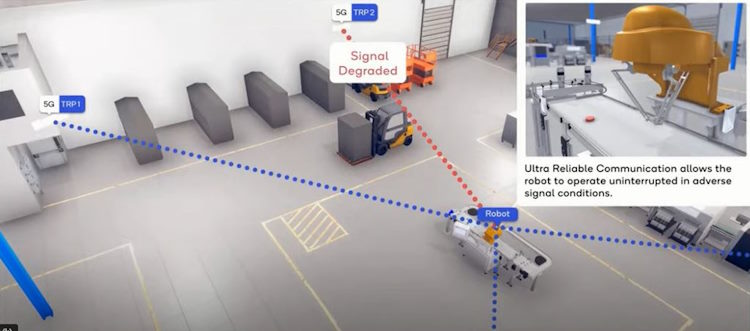
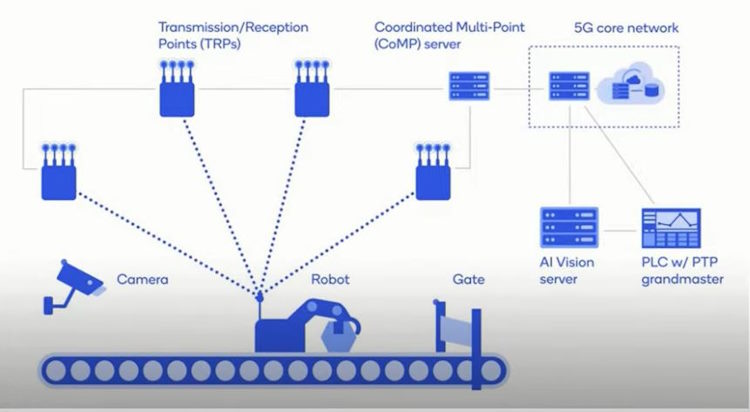
Robotics and Automation: Automated Warehouses: Utilize robotic systems for picking, packing, and sorting goods. Autonomous Vehicles: Employ drones and self-driving trucks for delivery and transportation.

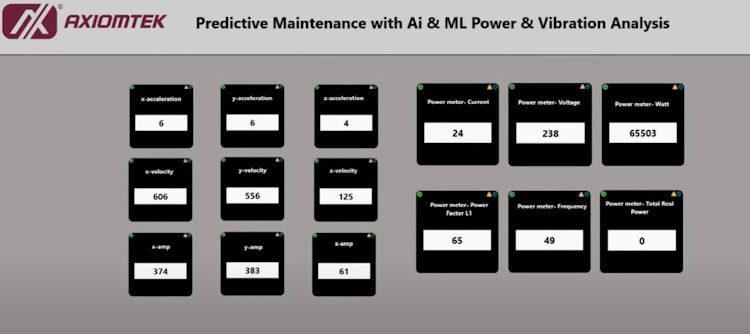
Vision AI for sushi detection is an example of shop floor AI that automatically counts the consumption of different types of sushi in retail restaurants. This provides real-time data to the central kitchen, enabling accurate stocking based on actual consumption patterns from various outlets. Since different outlets may have distinct eating or buying preferences for different types of sushi, this data helps tailor stock levels accordingly.
When AI analytics is applied over a period with sufficient data, it can effectively forecast future demand from different areas, ensuring better preparation for upcoming needs.
The above case demonstrated how AI is able to assist in the supply chain management process.
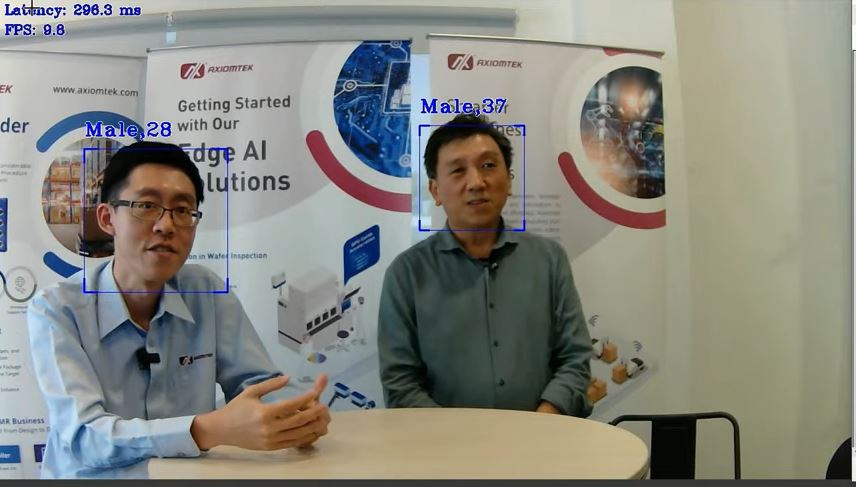
We showcased Vision AI’s capability to determine a person’s gender and age, which can be extracted at unattended kiosks or vending machines. These machines display videos or images that target the buying audience at remote locations.
if you want to watch this live click at the link below:-
AIoTmission Sdn Bhd, established in 2022 as a subsidiary of Axiomtek (M) Sdn Bhd, is a leading provider of technological training and consultancy services specializing in Artificial Intelligence (AI) and Industrial Internet of Things (IIoT) solutions. Our mission is to drive the Fourth Industrial Revolution (IR4.0) and facilitate digital transformation across Southeast Asia, including Malaysia, Singapore, Indonesia, the Philippines, Thailand, Vietnam, and Myanmar. At AIoTmission, we are dedicated to advancing research and development in AI and IIoT technologies, with a focus on industrial applications such as sensors, gateways, wireless communications, machine learning, AI deep learning, and Big Data cloud solutions. Through collaboration with our valued clients and partners, we deliver innovative solutions tailored to industry needs, enhancing technological capabilities and operational efficiency.